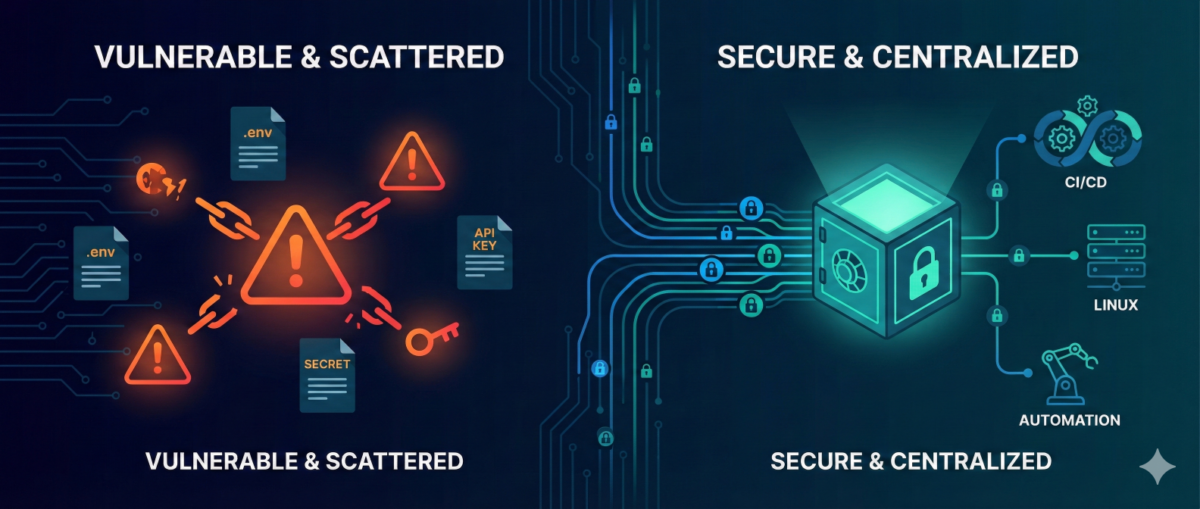
Secrets Management in DevOps: From .env Files to Enterprise-Grade Control
API keys. Database passwords. SSH private keys. OAuth tokens.
Secrets are everywhere in modern infrastructure—and they are one of the most common breach vectors.
In many environments, secrets still live in:
-
.envfiles -
CI/CD variables
-
shared password managers
-
copied Slack messages
-
or worse… Git repositories
As infrastructure scales, this approach becomes dangerous.
This guide explains how to evolve from ad-hoc secret handling to structured, auditable, and secure secrets management—without breaking pipelines or slowing teams down.
Why Secrets Become a Hidden Risk
1) Secrets Spread Faster Than Code
Developers copy:
-
.envfiles between machines -
API tokens into scripts
-
credentials into automation workflows
Soon, you lose track of:
-
where secrets are stored
-
who has access
-
which ones are still valid
2) Long-Lived Credentials = Long-Term Risk
Static secrets:
-
rarely rotated
-
shared across environments
-
reused in multiple systems
If leaked once, they remain valid until manually revoked.
3) Automation Amplifies Exposure
CI/CD pipelines, infrastructure-as-code, and workflow tools (like n8n) increase the number of systems that require credentials.
More automation = more secret sprawl if unmanaged.
The Principles of Modern Secrets Management
A mature approach is based on five principles:
1) Centralization
Secrets must live in a centralized secret store, not:
-
Git
-
local files
-
environment variables scattered across hosts
Centralization provides:
-
single control point
-
audit logs
-
policy enforcement
2) Least Privilege Access
Each system or service should only access:
-
the specific secret it needs
-
for the minimum duration required
Not:
-
“full access to all secrets in prod”
3) Short-Lived Credentials
Instead of static credentials:
-
use dynamic, time-limited secrets
-
generate database credentials on demand
-
issue temporary cloud tokens
If compromised, the blast radius is limited.
4) Automatic Rotation
Rotation should be:
-
scheduled
-
automated
-
transparent to applications
Manual rotation does not scale.
5) Full Auditability
You should be able to answer:
-
Who accessed which secret?
-
From which system?
-
At what time?
-
For what purpose?
If you can’t answer this, you have governance gaps.
Practical Architecture for DevOps Teams
You don’t need a massive transformation to improve security.
Phase 1: Remove Secrets from Git
-
Scan repositories for leaked credentials
-
Revoke exposed secrets immediately
-
Replace with environment injection from a secure store
This is the fastest risk reduction step.
Phase 2: Introduce a Central Secret Store
Adopt:
-
Vault-style systems
-
Cloud-native secret managers
-
Encrypted secret backends integrated with CI/CD
All pipelines should fetch secrets at runtime—not store them permanently.
Phase 3: Implement Dynamic Secrets for High-Risk Systems
Especially for:
-
databases
-
cloud IAM roles
-
production SSH access
-
automation service accounts
Dynamic credentials dramatically reduce breach impact.
Phase 4: Secure Automation Platforms (Including n8n)
Automation tools often become secret hubs.
Best practices:
-
store credentials in encrypted backend
-
restrict workflow-level access
-
separate dev/stage/prod secrets
-
audit workflow changes
-
restrict export permissions
Automation must not become a secret leakage vector.
Common Anti-Patterns
“Base64 encoding is enough.”
It is not encryption.
“Only Dev has access, so it’s safe.”
Internal threats and compromised laptops are real risks.
“We rotate once per year.”
In modern threat models, that is effectively static.
Incident Reality: Secrets Leak
When—not if—a secret leaks:
-
You must detect it quickly.
-
You must rotate immediately.
-
You must understand blast radius.
-
You must audit historical usage.
Without centralized management, this becomes chaos.
With structured secrets management, it becomes a controlled response.
Conclusion
DevOps accelerates delivery—but unmanaged secrets accelerate breaches.
Mature secrets management enables:
-
safer automation
-
reduced blast radius
-
audit-ready infrastructure
-
stronger Zero Trust posture
You don’t need perfection to start.
You need centralization, rotation, and visibility.
From .env files to enterprise-grade control—this is one of the highest ROI security upgrades any infrastructure team can implement.